If I’ve learned anything from researching those falsely accused is that it takes a very long time to get the courts to vacate unjustified convictions. So I just have to accept that and keep on keeping on.
Category: Litigation
bookmark_borderFalse Narrative
This Table:
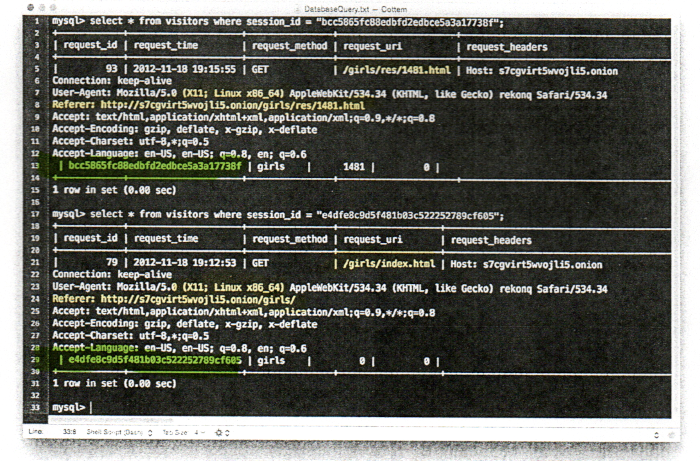
Does Not Support the Government’s Narrative:
On November 18, 2012, a user with IP address 69.207.147.71 accessed “Website A” and was presented with different sections to choose from and access further, including, but not limited to the following: “pre-teen boys”, “teen-aged boys”, “teen-aged girls”, “babies/toddlers”, and “fetishes”. The user with IP address 69.207.147.71 selected the section “PT girls”. After selecting the “PT girls” section, the user with IP address 69.207.147.71 was presented with the webpage with the title “/girls/pt girls” at the top of the page. Several board image threads were displayed on that page including thumbnail images from various threads. One of the threads, thread “1481”, had the subject title “finger bum girl” and displayed three thumbnail images from that particular thread. The images displayed included images with the file names dsc03248, dsc03286 and dsc03287. The images ending in 286 and 287 are close up pictures of a prepubescent vagina being digitally penetrated. The thread could be accessed by either clicking on the link to the thread with the subject “finger bum girl” or by clicking on one of the three images displayed. The user with IP address 69.207.147.71 then selected the 1481 thread with the identified subject, “finger bum girl”, and accessed a webpage that contained all the images available on that thread, consisting of over thirty pictures of a young girl, with many of them containing images depicting sexually explicit conduct. All the pictures would have appeared once the user clicked the 1481 thread with the identified subject, “finger bum girl”, or clicked on one of the three displayed thumbnail images.
Therefore, the conviction is invalid and is why I’m still litigating the matter today.
bookmark_borderI was railroaded
I (Kirk Cottom) was Railroaded
The meaning of being railroaded according to my computer’s dictionary is to “press (someone) into doing something by rushing or coercing them.”
The timeline of the railroading is such:
July 28, 2015: I fly out to Nebraska to see Mr. Becker’s “evidence book”.
July 29, 2015: I view the evidence book with my Attorney, Mr. Howard and his “expert”, Mr. Kasel. I’m not impressed and order Mr. Howard to prepare for the Daubert hearing and trial. (If I won the Daubert hearing the case was over, if I lost the hearing we would proceed to trial, both scheduled for August 3, 2015.) I fly back to Rochester that evening and return to work the next day.
July 30, 2015 (8am to 4pm): Mr. Howard e-mails me all day, trying to get me to agree to allow him to negotiate a plea I’d enter into if we lost the Daubert hearing on August 3, 2015. I repeatedly order Mr. Howard to prepare for trial and that he did not have permission to negotiate any plea deal. He then tries to call me on the phone, I refuse to answer.
July 30, 2015 (4pm to 6pm): A little after 4pm, Mr. Slawinski e-mails me and asks if I would come to his office, I agree. Once there I’m ambushed by him, Mr. Howard and Mr. Gross to accept a “conditional plea” deal, that none of them had permission to negotiate. They coerce me into agreeing to the conditional plea by convincing me that it was like a “Nolo contendere” plea, when they knew that it wasn’t.
August 1, 2015: I fly back to Nebraska and inform Mr. Howard I don’t like the plea deal. He says lets focus on winning the Daubert motion.
August 3, 2015: I lose the flawed Daubert hearing. It was flawed because both the government and the defense experts perjured themselves on multiple issues. Their lies included:
1) Stating that the FBI’s Network Investigative Technique (NIT) was just the “exploit code”. (In my case a flash application.) This lie was debunked in subsequent litigation. (The FBI tried this false narrative again while prosecuting “Operation Pacifier” cases, based on the infamous “playpen” website. All those cases rejected this false narrative and adjudicated that the NIT consisted of 4 parts. That was “prejudicial” because my Daubert hearing was based on a knowingly false narrative.)
2) That perjury, exposed many others. Like lying about the code on TB2’s server. Those lies included: claiming that Tinyboard (the software that ran TB2) had a visitors table, claiming that Tinyboard issued sessionID’s to clients and claiming both the fraudulent items were admissible at trial when they knew they were both inadmissible per FED. R. EVID 803(6) & 803(8). That cause Mr. Becker’s team to present that data as “Expert Summary Evidence” to circumvent its exclusion from trial.
3) All Those perjuries helped hide the biggest perjury of this case, the fact that the NIT report (and it’s underlying documents, Dr. Edman’s computer logs, populated by his scripts) do not provide any evidence for a crime, because none of it has any information about images. This means that the Nebraska indictment was fraudulently obtained and thus invalid.
Since all the above is irrefutable, it is absolute proof that I was railroaded.
bookmark_borderMalicious Prosecution
November 17, 2012: Keith Becker’s team fraudulently obtains a “void ab initio” Network Investigation Technique (NIT) warrant. It was fraudulent because the data they said they were obtaining was going to be fabricated and falsified; and, even if it wasn’t, all the data would be inadmissible at trial per Federal Rules of Evidence 803(6) & 803(8). (Rule 803(6) prohibits documents that are created for the sole purpose of litigation and rule 803(8) prohibits police reports.)
The warrant was void ab initio because the Magistrate in Nebraska had no authority to issue a warrant to search a computer in New York.
November 18, 2012: my linux computer sends a “computer under FBI control” two encrypted messages. One at 7:13pm CST and then another at 7:16pm CST. Each message was 98 characters and contained similar information. Both messages labeled board_id as “2” and method as “swf”. The only difference between the two messages was what they called a “session”. The session for the 7:13pm message was e4dfe8c9d5f481b03c522252789cf605 and for the 7:16pm message is was bcc5865fc88edbfd2edbce5a3a17737f.
January 18, 2013: Mr. Becker’s team generates a “TB2” NIT report. It consists of 3 pages. The source of the information on the first page was Time Warner, it indicated that the IP in question was assigned to my house at the time of the alleged crime. The source of the information on the second page was Dr. Edman’s fabricated “visitors” table that he populated with falsified information with a script he called gallery.php. The source of the information on the third page was also provided by a fabricated table and populated with a script (cornhusker.py) that Dr. Edman coded solely for criminal prosecution.
The federal rules of evidence mentioned above clearly prohibit the use of Dr. Edman’s tables at trial. Since the Becker team knew this, they presented this data in their NIT Report as “Expert Summary Evidence” and failed to disclose the source of the information on pages 2 and 3 of their report, on purpose, to evade those federal rules of evidence. This conduct established bad faith.
March 20, 2013: Mr. Becker’s team fraudulently obtains an indictment from a grand jury in Nebraska based solely on the NIT Report that they generated on January 18, 2013.
That created many problems for Mr. Becker’s team:
1) As mentioned above, the federal rules of evidence clearly preclude this evidence from trial. That makes any indictment obtained solely with that NIT report potentially frivolous. (If the government obtains an indictment with evidence that is inadmissible at trial, it must believe that it will probably find admissible evidence before trial.)
2) Mr. Becker’s team has testified that page 2 of their NIT report (Dr. Edman’s fabricated and falsified “visitors” table) is evidence of a crime. Specifically, they testified that it was proof that a web browser running on my linux computer viewed illegal images on a website called TB2, because it loaded two html files, one called “index.html” at 7:12pm CST and then another named “1481.html” at 7:15pm CST. Unfortunately, this is a claim that is easily debunked. As Gerry Grant testified at US v. Raymonda’s suppression hearing in 2013, when you view a webpage, your browser makes a series of “GET REQUESTS”. First, it requests the html file. After it receives it, it then requests the other items to finish the page, among these other requests are “image” requests. Most browsers are configured to automatically make these requests for images, BUT you can configure the browser NOT to make them. You can also configure the browser to ignore java, javascript and flash application requests.
The only way to know if a given IP requested a given file is to view the web server’s logs. In the case of TB2’s server, those logs would be useless as the only IP in its logs would be the last node the traffic went through. (TB2 was being hosting on a type of VPN called the Onion Router or TOR). Therefore any testimony given before the grand jury in Nebraska that the FBI’s NIT report provided evidence of a crime was perjury as it only contained evidence that index.html and 1481.html were requested. Dr. Edman’s visitors table doesn’t provide ANY evidence that ANY images were requested, thus it doesn’t provide any evidence that a crime was committed. In other words, viewing those HTML files would never be a crime, because they are just text files.
3) The only thing that ties that non-criminal activity (requesting index.html and 1481.html) to my IP address is Dr. Edman’s cornhusker.py log that’s presented on the NIT Report’s third page. As mentioned above, this page would be inadmissible at trial because it was created by law enforcement, solely for prosecution. As mentioned above, this log suggests that the FBI’s flash application was running on my linux computer at 7:13pm CST and 7:16pm CST and that flash app sent those two encrypted messages after being requested by my browser after loading those two html files at 7:12pm CST and 7:15pm CST.
As you can see the FBi’s narrative has five major flaws:
1) As explained above, page 2 doesn’t provide any probable cause to believe a crime has been committed.
2) Page 2 is based on a fabricated table (TB2 runs of PHP software called Tinyboard, Tinyboard doesn’t have a visitors table).
3) That fabricated table contains falsified evidence (Tinyboard doesn’t generate sessionIDs for visitors). The request_uri is also falsified. This forgery makes it impossible to determine the actual proceeding page. It means they cannot testify, in good faith, about a visit progression because their visitors table reports that the request_uri is the same page as the referring page. (For example: normally when you click a link for page B on page A the request_uri will be page B and the referring page will be page A. The forgeries generated by Dr. Edman’s scripts on TB2 always show the request_uri as page B and the referring page as page B)
4) Dr. Edman’s fabricated tables, and the falsified information he puts in them, are a form of perjury.
5) There is a strong possibility that none of this information was generated by human action. That is because the flash application takes too long to execute. The logs state that the flash application for “session” e4dfe8c9d5f481b03c522252789cf605 took 39 seconds to execute and for “session” bcc5865fc88edbfd2edbce5a3a17737f it took 63 seconds. Now, in human time that isn’t too long, but in the world of computers that’s a ridiculously long amount of time. Here are the sequence of events:
- At 7:12pm my browser requested index.html. According Dr. Edman’s table, his script, gallery.php was loaded at 7:12:53 in a hidden iframe.
- gallery.php then presented the browser with javascript to load Dr. Edman’s gallery.swf that the browser would execute it immediately.
- once the flash app was loaded it would make a dns query for the IP of the server that was running Dr. Edman’s cornhusker.py (a server that the FBI destroyed)
- the dns request was ridiculously long. It was 96.126.124.96.(98 character encrypted text).cpimagegallery.com and it negated the need to establish a socket connection to cornhusker.py, because the dns request reveals the true IP and the falsified sessionID.
- Regardless, cornhusker.py should have responded to the requests in milliseconds and then the flash app would request permission to communicate milliseconds later. Therefore the whole transaction should have taken less than 3 seconds. However, the first transaction took 39 seconds and the second took an astonishing 63 seconds. In the world of DNS, every request after the first should be much faster than the first. The fact that it took significantly longer strongly suggests shenanigans were afoot.
- We’ll never be able to determine what happened because the FBI destroyed the server (along with its logs) that could shed light on this egregious anomaly.
It’s abundantly clear that Mr. Becker’s team presented the Nebraska grand jury with false information and that information was the sole basis for the indictment. That means that the indictment was obtained fraudulently. Therefore the whole prosecution was malicious and must be vacated.